Scams, attacks, and hacks have long existed in the cryptocurrency sector. While some hacks have indeed been executed for blatant stealing, others have been done to make networks aware of their weaknesses. While most hackers operate covertly and alone, some join cults.
As security tightens and firms start to implement more security measures, attackers lay down plans for more complex attacks. In one of the recent blogs by Microsoft security threat intelligence, the team identified a threat actor tagged as DEV-0139. DEV-0139 hunts cryptocurrency investment firms using Telegram chat groups.
Binance’s CZ also recently tweeted about the attack, asking users to stay cautious and refrain from downloading files from unknown sources.
How does DEV-0139 carry out the attack?
DEV-0139 basically frames out his attacks by joining Telegram chats where the cryptocurrency exchanges and their VIP clients converse. DEV-0139 then impersonates a representative of another cryptocurrency investment firm. The attacker then redirects the clients to a different chat. The chat will be used to then ask for feedback on the cryptocurrency exchange fee structure.
DEV-0139 then uses their broader experience and knowledge of the cryptocurrency industry to gain trust and lure them into the trap. The attacker will send a weaponized Excel file, OKX Binance & Huobi VIP fee comparision.xls, to the client. The file will have a list of tables that include the fee structure of various cryptocurrency exchanges. This increases the credibility and trust of the attacker, fooling clients. The weaponized file then begins to work its game.
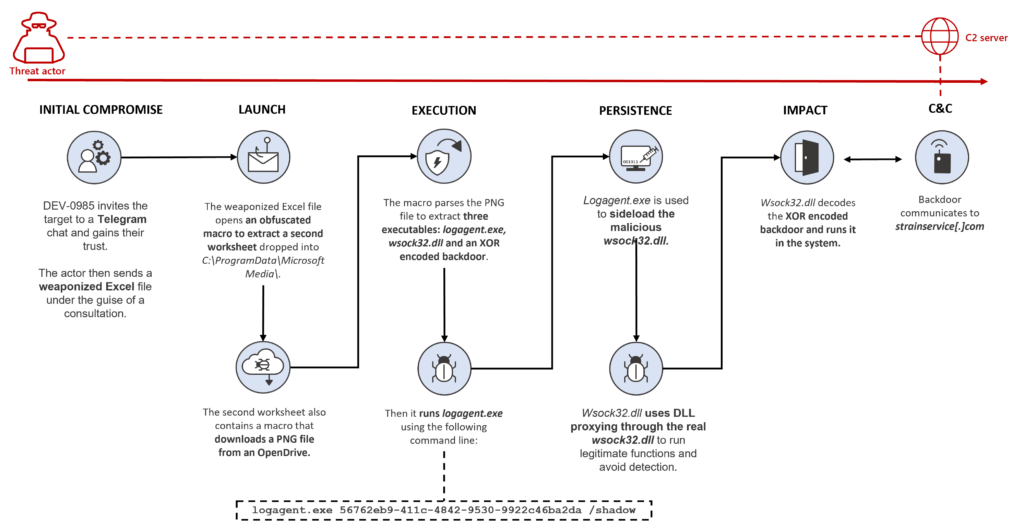

It initiates its attack by carrying out a slew of activities. The initial attack begins by dropping another Excel sheet that uses a malicious program to retrieve data. The execution of the sheet will happen in “invisible mode” and downloads a PNG file. The PNG file will have three executables: a legitimate Windows file named logagent.exe, a malicious version of the DLL wsock32.dll, and an XOR-encoded backdoor.
The infected system can then be accessed by the attacker from the backdoor remotely. The attacker then uses it to collect all data necessary to loot the victim’s cryptocurrencies.





