In 2021, cybercriminals had a banner year, taking $3.2 billion in cryptocurrencies. This number is sure to be topped in 2022 as per the latest study by Chainalysis, the popular blockchain data, and analysis firm. According to the data, hackers have stolen $1.3 billion from exchanges, platforms, and private companies in the first three months of this year, with the victims being predominantly in DeFi.
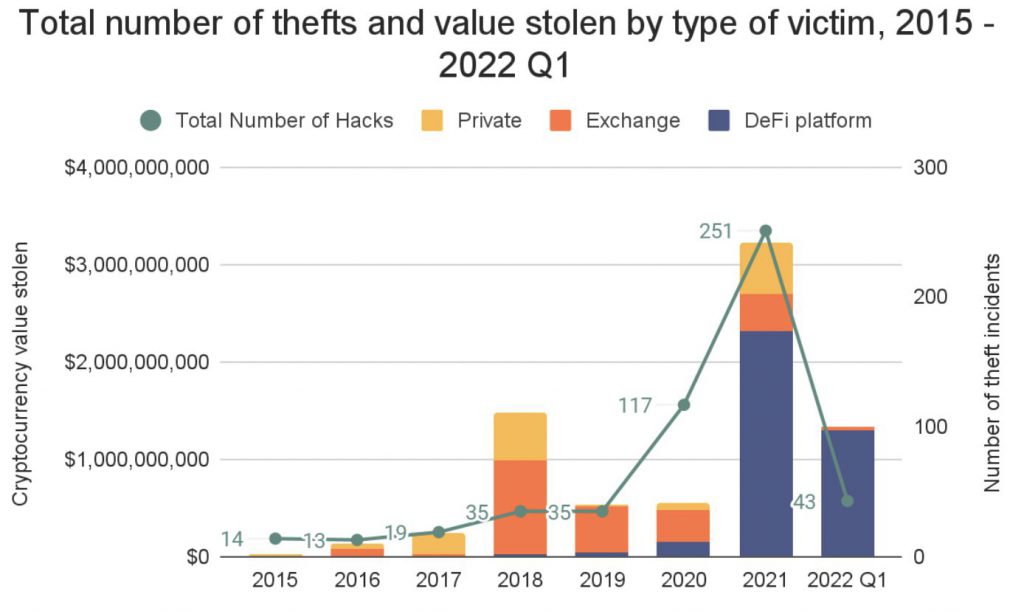

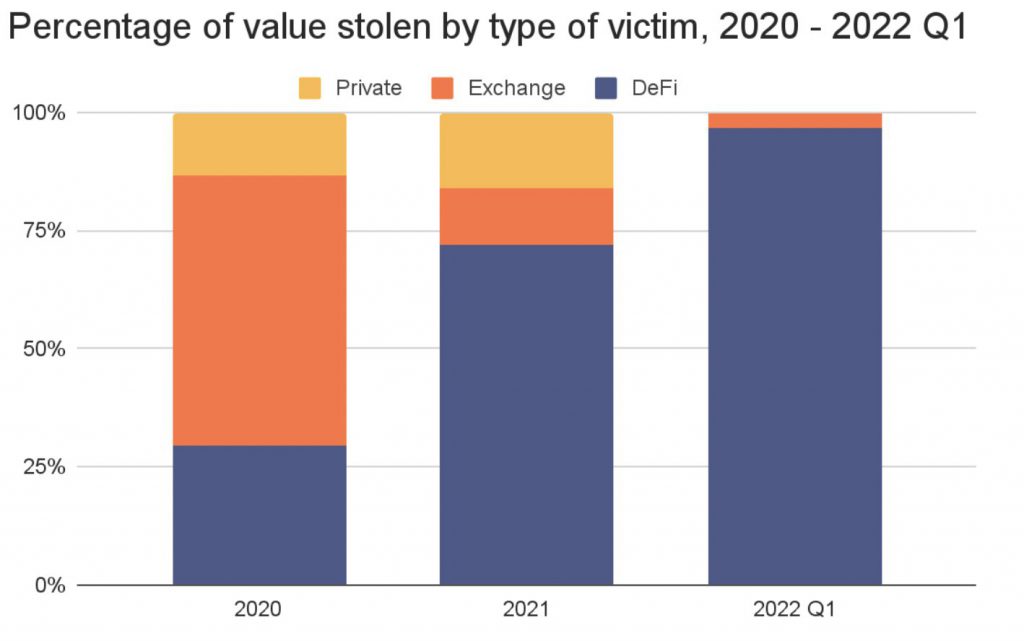
DeFi protocols were the largest hit, being responsible for nearly 97% of all cryptocurrency stolen in the first three months of 2022, up from 72% in 2021 and just 30% in 2020. DeFi platforms have been the target of 7 of the 10 greatest attacks in the last fifteen months. The seven DeFi attacks resulted in a $1.6 billion loss, whereas the three exchange hacks resulted in a $960 million loss.

How have hackers exploited Defi platforms?
Security breaches in which hackers obtained access to victims’ private keys—the crypto-equivalent of pickpocketing—were the main cause of cryptocurrency attacks in the past. The March 2022 hack of Ronin Network, which resulted in the theft of $615 million in bitcoin, demonstrated the technique’s continued effectiveness. Security breaches resulted in the theft of 35% of all cryptocurrency worth from 2020 to Q1 of 2022.
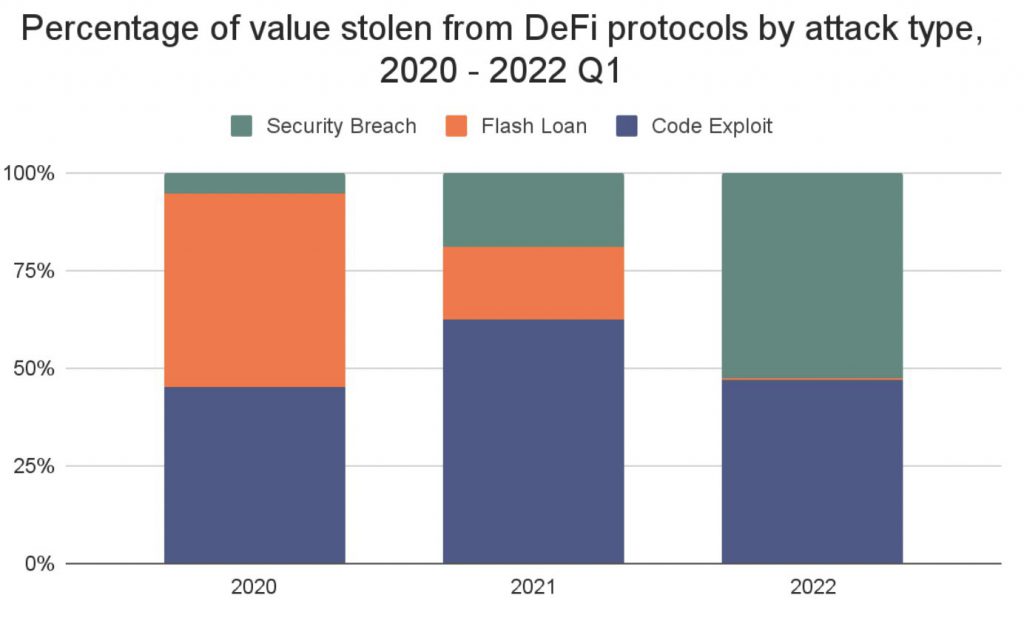
According to Chainalysis, the most common source of theft is incorrect coding. Outside of the Ronin attack, code exploits and flash loan attacks—a sort of code exploit involving the manipulation of cryptocurrency prices—have accounted for the majority of the money taken.
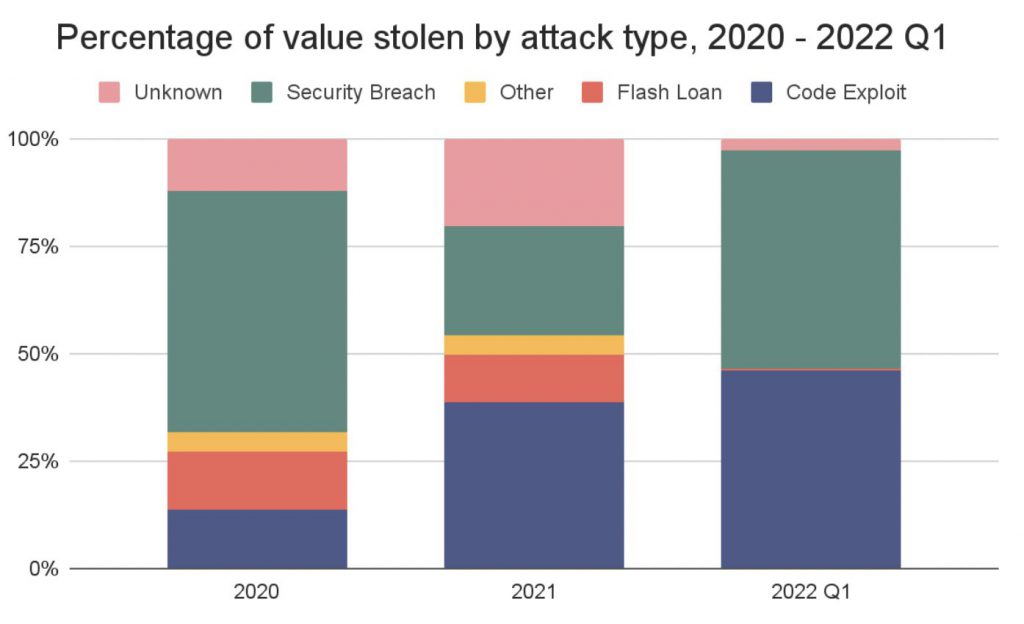

Code exploits can happen for a variety of reasons. For one thing, open-source development is a cornerstone of DeFi applications, in keeping with the company’s belief in decentralization and openness. This is a significant and generally beneficial trend: because DeFi protocols do not require human intervention to shift funds, users should be able to audit the underlying code in order to trust the protocol. Cybercriminals, on the other hand, benefit from this since they can examine the scripts for vulnerabilities and design exploits ahead of time.
30% of code exploits and 73% of flash loan attacks took place on platforms audited during the last year.

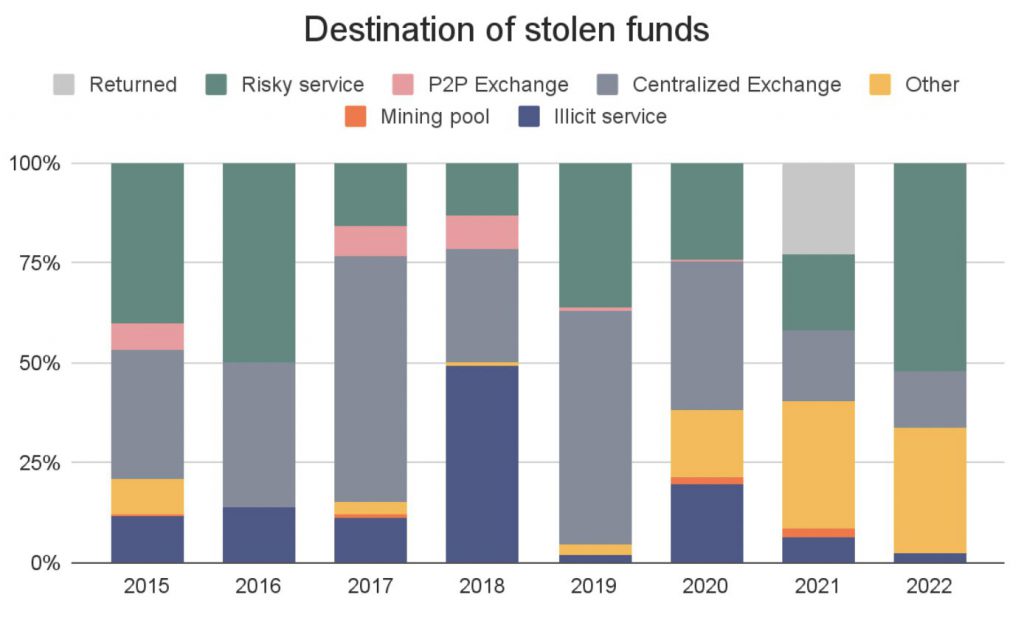
How do hackers launder stolen cryptocurrency?
More stolen cash was directed to DeFi platforms (51%) and dangerous services (25%) in 2021 than ever before. Previously a popular destination for stolen assets, centralized exchanges have fallen out of favor, garnering less than 15% of the total. This is most likely owing to exchanges’ embracing of AML and KYC protocols, which jeopardize cybercriminals’ anonymity.
This year, Chainalysis added a new category to reflect what could be a first among the cryptocurrency exchange hacks we’ve seen: returns. The criminal behind the $600 million Poly Network hack returned all $613 million in stolen assets in August of last year, and turned down a bug bounty offer.

The risk of exploitation grows as the total value locked in DeFi rises to new all-time highs — $256 billion at the most recent peak. The necessity for smart contract security and pricing oracle accuracy is one takeaway from the exponential surge in thefts from DeFi systems. Code audits, decentralized oracle providers, and a more rigorous approach to platform security may be the most effective ways to achieve this goal.
Fortunately, blockchain analysis can help even if these processes fail and cryptocurrencies are taken. Investigators who have a complete picture of how money moves from one address to the next can take advantage of opportunities to freeze or seize assets in transit, preventing criminal actors from cashing out.





