A year back, the likes of Terra, Avalanche, Fantom, etc were still upcoming projects in the digital asset space. Right now, these protocols are illustriously involved in the DeFi ecosystem, handling billions in value. From March 2021 to March 2022, the estimated TVL reached $215 billion, rising 156% in a year. However, with innovation came excessive intrusion. Crypto Crimes reached a new height in Q1 2022, as over $1.2 billion in assets were stolen.
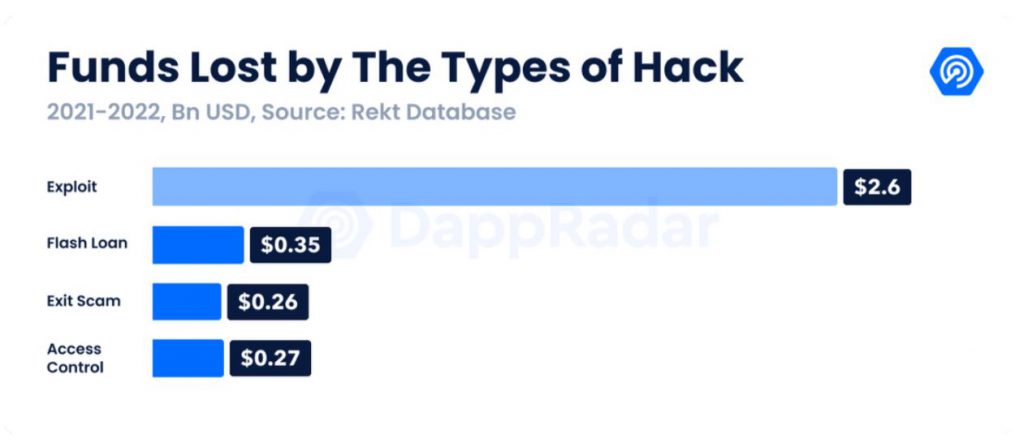

From the Ronin hack to the Solana Wormhole exploit, hackers’ targets stemmed down to one particular pool; blockchain bridges.
Blockchain Bridges in DeFi; chink in the Armor?
Bridges were developed to connect two different DeFi networks in order to improve interoperability functions. In this manner, digital assets and NFTs, within individual chains could be moved across different blockchains, with the option to utilize these assets.
Now the security aspect of these DeFi bridges is categorized into two different types; trusted and trustless bridges. Trusted bridges require and rely on a third party to validate transactions. The party functions like a custodian. While Trustless bridges are completely dependent on smart contracts and certain algorithms. While trustless bridges may appear more decentralized and safe, both categories were exploited in the recent hacks.
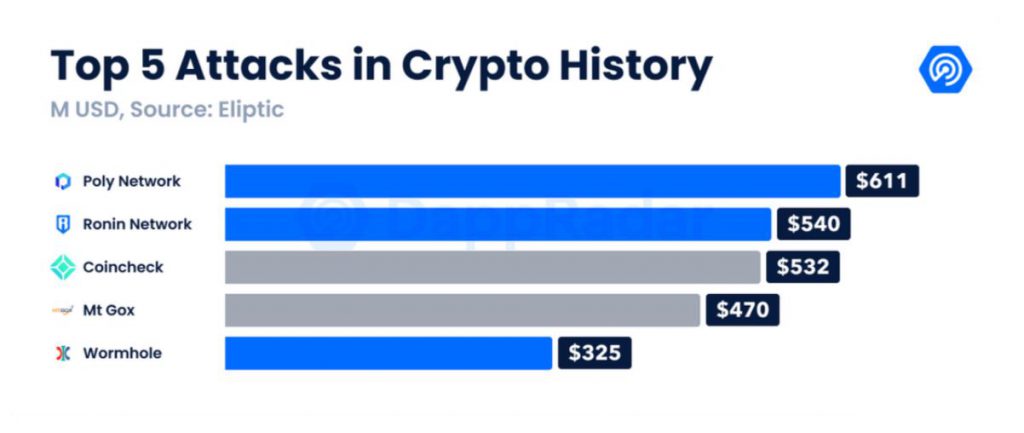

i) Ronin DeFi hack
According to an analysis by DappRadar, Ronin bridge utilizes a multi-sig wallet for custody of bridged assets. For verification, it requires multiple cryptographic signatures. Ronin sidechain had nine validators, and it needed five different signatures to approve deposits or withdrawals. Safe enough right? Nope.
While the five signatures should have been controlled by different parties, four signatures were held by the Sky Mavis team alone, which was its single point of attack. The hacker managed to gain control of four signatures at once and only needed one more to inflict an exploit. On 23rd March, Axie DAO’s signature was accessed, and the attacker completed his five signatures. 25.5 million USDC and a whopping 173,600 ETH were siphoned within two different transactions. The concerning part was that the Sky Mavis team recognized the DeFi attack after a whole week, which raises questions about their monitoring mechanism as well.
ii) Solana Wormhole Attack
While trusted bridges had a fundamental flaw of human deficiency in the above attack, Solana’s Wormhole was a faulty bug in the custodian smart contract. A flaw in the code, allows the hackers to devise the cross-chain validators. The attacker sent 0.1 ETH from Ethereum into Solana to trigger a set of “transfer messages” that tricked the program into approving a supposed 120,000 ETH deposit.
What is the Ideal way forward?
As explained above, both trusted and trustless bridges require further upgrades to minimize such technical pitfalls. The repercussions are worth billions of dollars, and DeFi Demand is only beginning to rise.
In the case of trusted bridges, it is fairly obvious that validator signatures need to be increased in terms of the ratio for approval. For trustless bridges, bugs and other technical constraints need to be minimized to avoid risky situations.
Overall, the development in the DeFi space has to be more collective. Protocols like Animoca Brands, Binance, and other Web3 brands raised $150 million to help Sky Mavis reduce its financial losses post Ronin hack. Such community support needs to pan out in terms of improving network health, auditing code, and creating a better approach toward L1, and L2 solutions.





