High-Level Comparison: Permissionless vs Permissioned Blockchains
Blockchain technology has revolutionized various industries, offering decentralized and secure solutions for transactions, data management, and authentication.
Two primary types of blockchains, permissionless and permissioned, have emerged to cater to different needs and use cases.
In this article, we will explore the differences between permissionless and permissioned blockchains, their key features, pros and cons, and their applications in various industries.
Let’s delve into the world of blockchain technology and understand how permissionless and permissioned blockchains differ.
Also read: Shiba Inu: BONE Surges 5.3% While Memecoins Decline
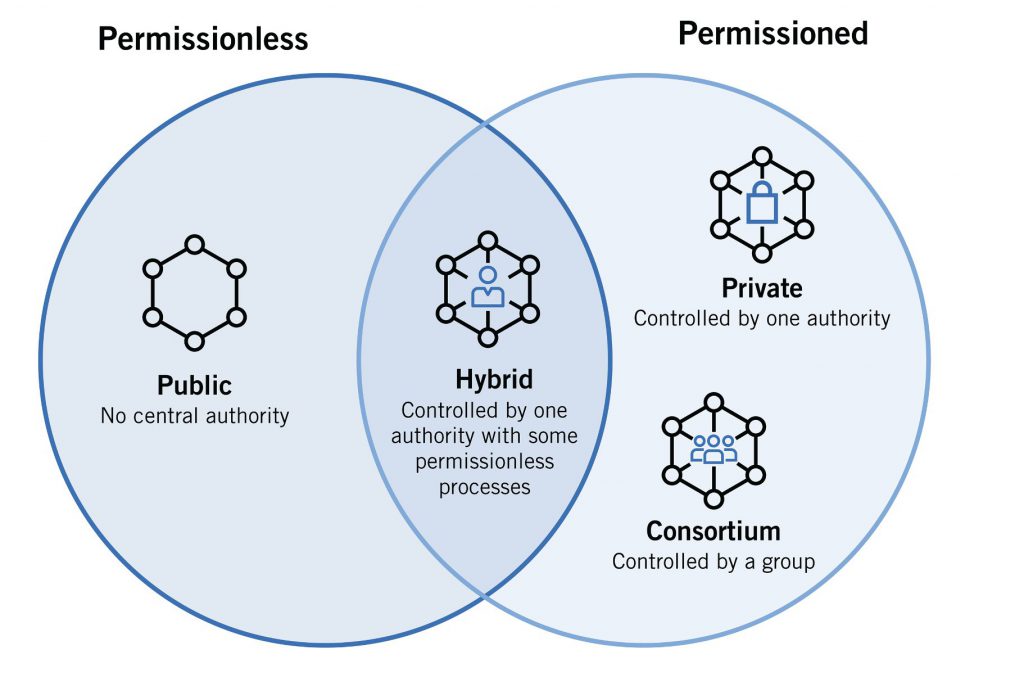

Permissionless vs Permissioned Blockchains
Permissionless Blockchain
What is a permissionless blockchain?
Permissionless blockchains, also known as public blockchains, are open networks that allow anyone to participate in the consensus process and validate transactions and data.
In a permissionless blockchain, there is no central authority controlling access or participation.
Furthermore, the key characteristic of a permissionless blockchain is its radical decentralization, where transactions are transparent, development is open source, and there is no central authority governing the network.
Also read: Ethereum is Down 30% Against Bitcoin As Vitalik Buterin Moves 600 ETH
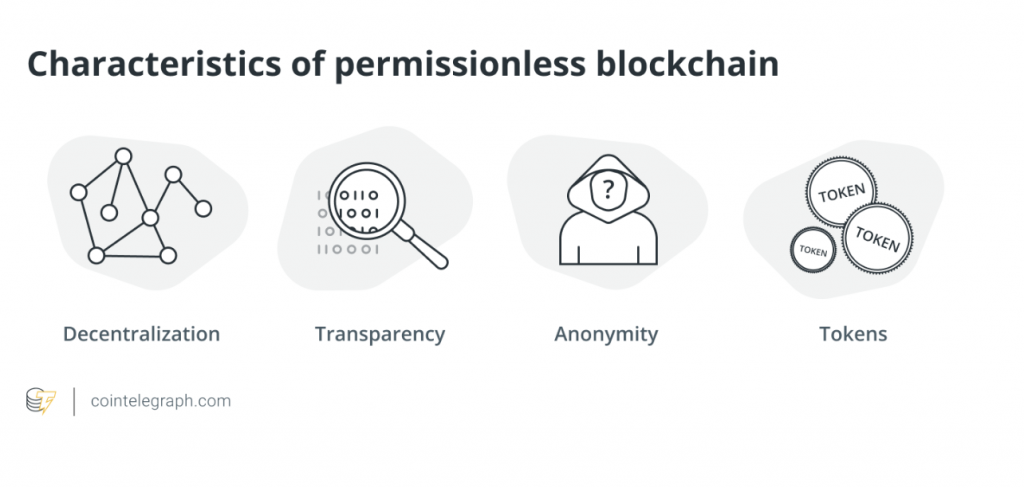
Key Characteristics of Permissionless Blockchains
Full Transparency of Transactions: Permissionless blockchains offer complete transparency, allowing all participants to view and verify transactions on the network. This transparency enhances trust and accountability in the system.
Open Source Development: Permissionless blockchains encourage open source development, where anyone can contribute to the improvement and innovation of the blockchain. This collaborative approach fosters community-driven growth and ensures continuous development.
Anonymity, with Some Exceptions: While permissionless blockchains provide a certain level of anonymity, it is important to note that transactions are not completely anonymous. Some exceptions exist, such as pseudonymous user identities, which can be traced to a certain extent.
Lack of Central Authority: Permissionless blockchains operate without a central authority governing the network. The absence of a central authority allows for a more democratic and decentralized decision-making process.
Heavy Use of Tokens and Digital Assets: Permissionless blockchains often rely on tokens and digital assets as incentives for participants. These tokens can be used for various purposes, such as voting rights, access to services, or rewards for contributing to the network.

Pros and Cons of Permissionless Blockchain
Pros
Broader Decentralization: Permissionless blockchains offer a high level of decentralization. This enables a larger number of participants to join the network compared to permissioned blockchains.
Transparency: The transparent nature of permissionless blockchains facilitates faster reconciliation and enhances trust among participants.
Resistance to Censorship: Permissionless blockchains are resistant to censorship due to their broad accessibility and participation across locations and nationalities. This feature promotes freedom of expression and financial inclusivity.
Strong Security: Permissionless blockchains are inherently secure. Attackers cannot easily target a single repository. This makes it difficult to corrupt the majority of the network and disrupt consensus mechanisms.
Cons
Poor Energy Efficiency: Permissionless blockchains can be resource-intensive due to the network-wide verification of transactions, resulting in poor energy efficiency.
Lower Performance and Scalability: The verification process in permissionless blockchains can strain computing resources, leading to lower performance and scalability compared to permissioned blockchains.
Less Privacy and User Control: Permissionless blockchains provide less privacy and user control over information, as transactions and data are transparent and visible to all participants.
Permissioned Blockchain

What is permissioned blockchain?
In contrast to permissionless blockchains, permissioned blockchains, also known as private blockchains or permissioned sandboxes, are closed networks where access and participation are limited to designated parties.
Additionally, permissioned blockchains often operate in private enterprise contexts, where data management and security are of utmost importance.
These blockchains are partially decentralized, as they are distributed among known participants rather than unknown participants.
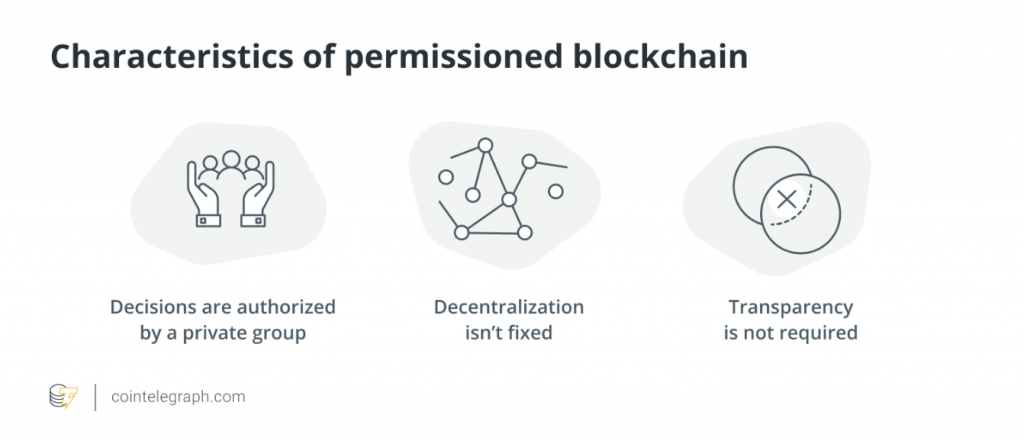
Key Characteristics of Permissioned Blockchains
Controlled Transparency Based on Goals: Permitted blockchains provide controlled transparency, allowing organizations to define the level of transparency based on their specific goals and requirements. This flexibility enables privacy and confidentiality when handling sensitive data.
Development by Private Entities: Permissioned blockchains are generally developed and managed by private entities. This allows organizations to have more control over the blockchain’s design, rules, and operations.
Lack of Anonymity: Unlike permissionless blockchains, permissioned blockchains do not prioritize anonymity. Participants in a permissioned blockchain are known and authenticated, which enhances accountability and traceability.
Lack of Central Authority, but Authorized Decisions: Permitted blockchains operate without a central authority, but decisions are authorized by a private group or consortium. This governance structure ensures that the network’s operations align with the objectives of the participating organizations.
Pros and Cons of Permitted Blockchain
Pros
Incremental Decentralization: Permissioned blockchains offer incremental decentralization, allowing multiple businesses to participate without the risks associated with highly centralized models.
Strong Privacy: Permissioned blockchains prioritize privacy, making them suitable for applications that require confidentiality and secure handling of sensitive information.
Customizability: Permissioned blockchains can be customized to specific use cases, allowing for diverse configurations, modular components, and hybrid integrations.
Performance and Scalability: Permissioned blockchains often exhibit better performance and scalability compared to permissionless blockchains. This is due to the limited number of nodes managing transaction verification and consensus.
Cons
Increased Risk of Corruption and Collusion: Since permissioned blockchains have fewer participants, there is a higher risk of corruption and collusion compared to permissionless blockchains.
Consensus Easily Overridden: In permissioned blockchains, the owners and operators have the ability to change the rules of consensus, immutability, and mining, making consensus easier to override.
Less Transparency for Outside Oversight: Permitted blockchains have limited participants, and the network’s operators determine privacy requirements, resulting in less transparency for external oversight.
Use Cases for Permissionless and Permissioned Blockchains


Both permissionless and permissioned blockchains have their own set of use cases based on their characteristics and strengths. Let’s explore some common use cases for each type of blockchain.
Permissionless blockchain use cases
A permanent blockchain’s use is typically in applications that require a high level of decentralization, transparency, and censorship resistance. Some common use cases include:
Digital Asset Trading: Permissionless blockchains serve as platforms for decentralized digital asset trading, allowing users to trade cryptocurrencies without the need for intermediaries.
Crowdfunding and Donations: Permissionless blockchains enable transparent crowdfunding campaigns and donations, ensuring accountability and trust in the process.
Distributed File Storage: Permissionless blockchains’ use can be for distributed file storage solutions, providing secure and decentralized storage options.
Permissioned Blockchain Use Cases
Permissioned blockchains find applications in industries that prioritize privacy, security, and controlled access to data. Some common use cases include:
Supply Chain Provenance Tracking: A persistent blockchain’s use is to track and verify the provenance of goods in supply chains, ensuring transparency and authenticity.
Claims Settlement: Insurance companies can leverage permissioned blockchains to streamline the claims settlement process, reducing fraud and enhancing efficiency.
Identity Verification: Permissioned blockchains offer secure identity verification solutions, enabling reliable and tamper-proof authentication in various sectors.
Choosing Between Permissionless and Permissioned Blockchains
Choosing the right type of blockchain for your project depends on several factors. Consider the following criteria when deciding between permissionless and permissioned blockchains:
Scalability and Performance: Evaluate the frequency and design of transactions and interactions with the blockchain to determine which type of blockchain can meet your scalability and performance requirements.
Power Consumption: Consider the computational and environmental costs associated with consensus mechanisms, as this can impact the energy efficiency of the blockchain.
Roles and Governance: Assess how organizations and stakeholders allocate power, make decisions, set permissions, and collaborate on the blockchain. This will help determine if a permissioned or permissionless blockchain aligns better with your governance structure.
Privacy and Anonymity: Determine the level of privacy and anonymity required for your project. Permissioned blockchains provide stronger privacy controls, while permissionless blockchains offer more transparency.
Technology Landscape: Consider existing systems and infrastructure, as well as the technical requirements for integration, cloud adoption, and edge computing.
Smart Contract Viability: Evaluate the need for smart contracts in your project and ensure that the chosen blockchain supports the required functionality for accountability and liability.
Tokens and Digital Assets: Determine if the use of tokens or digital assets is relevant to your project, as this can influence user incentives and behavioral economics.
Talent and Culture: Assess the availability of technical, design, and legal resources, as well as the willingness of stakeholders to adopt blockchain technology. Consider the cultural readiness for change and the level of trust in decentralized systems.
By carefully considering these criteria, you can make an informed decision on whether to choose a permissionless or permissioned blockchain for your project.
Conclusion: Permissionless vs Permissioned Blockchains
In conclusion, Permissionless vs Permissioned Blockchains has many differences. Permissionless and permissioned blockchains offer distinct features and functionalities, catering to different needs and use cases.
While permissionless blockchains prioritize decentralization, transparency, and censorship resistance, permissioned blockchains prioritize privacy, security, and controlled access to data.
Understanding the differences between these two types of blockchains is crucial when deciding which one to adopt for your project. Consider the specific requirements of your industry, the level of transparency needed, the need for privacy and control, and the scalability and performance requirements.
With this knowledge, you can harness the power of blockchain technology and select the right blockchain for your business needs.