Hacks and scams aren’t new to the crypto industry. However, an insider carrying out an attack on their own network is a rare case. A prominent crypto market maker, Wintermute was recently hit with a $160 million attack. The hacker managed to exploit a bug in the firm’s smart contract which further gave the hacker a chance to eliminate 70 different tokens. However, now, an elaborate analysis of how the hack could have been carried out by an internal party has surfaced.
James Edwards aka Librehash shared a Medium post alleging the Wintermute hack was an inside job. He pointed out how the existing conjectures focused on an externally owned address or EOA that decided if anything was “compromised” by using a flawed online vanity address generation service, the team’s use of the Wintermute smart contract was itself compromised.
Edwards further suggested that the theory is that the attacker was able to invoke the Wintermute smart contract, which presumably had admin access, by obtaining the private key for that EOA. But, there was no evidence of uploaded, verified code for the smart contract that was at play. This further elevated transparency concerns surrounding the firm.
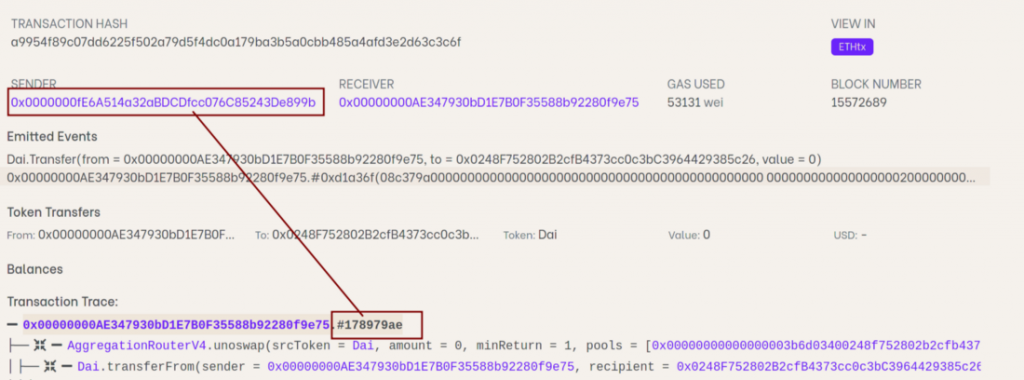

Additionally, after manually decompiling the smart contract code, Edwards conducted a more thorough study and claimed that the code did not correspond to the events that have been credited to have caused the attack.
Transfer of 13.48 million USDT post-Wintermute hacks elevates suspicion
It looks like this wasn’t the only thing that made Edwards doubtful about the hack being carried out by a third party. A transfer of 13.48 million USDT from the Wintermute smart contract address to the 0x0248 smart contract formulated and monitored by the hacker was brought to light.
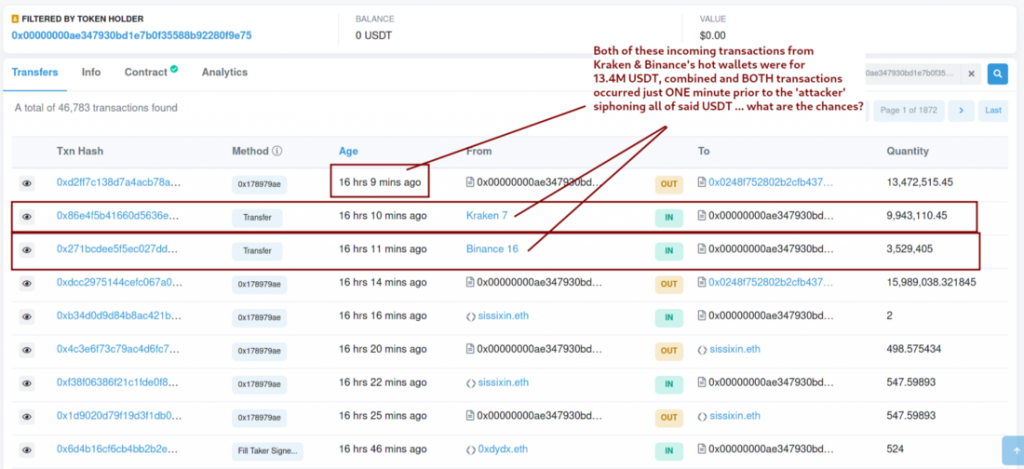

As seen in the above image, the compromised smart contract reportedly amassed two deposits from Kraken and Binance’s hot wallets. Edwards further added,
“It’s safe to assume that such a transfer must have been initiated from team-controlled exchange accounts.”
Additionally, the whole amount of Tether was manually transferred from the wallet to the 0x0248 smart contract in less than a minute after the compromised Wintermute smart contract got more than 13M USDT in cash. The 0x0000000fe normal wallet address reportedly ticked off this transfer.
It should be noted that the latest post is Edwards’s first analysis piece and is reportedly not a researcher or an analyst. However, he isn’t the only one that believes the hack was an inside job. While Wintermute has remained mum about it, Crypto Twitter certainly has not.





